Introduction
Authentication has come a long way from the days of simple passwords. Today, our digital lives are safeguarded by a plethora of authentication methods, from biometrics to One-Time Passwords (OTPs). Yet, despite these advancements, cybersecurity threats are proliferating at an alarming rate. Many businesses, while embracing technology, often overlook the vulnerabilities inherent in traditional authentication methods.
The solution? Multi-factor authentication (MFA), is a multifaceted approach to security that combines various authentication mechanisms. But how can organizations balance robust security with a user-friendly experience? That’s where Single Sign-On (SSO) enters the picture. In this exploration of MFA vs. SSO, we’ll dissect these two authentication strategies and illustrate how they can empower businesses to grow, fortify their defenses, and enhance the user journey.
What is Multi-Factor Authentication (MFA)?
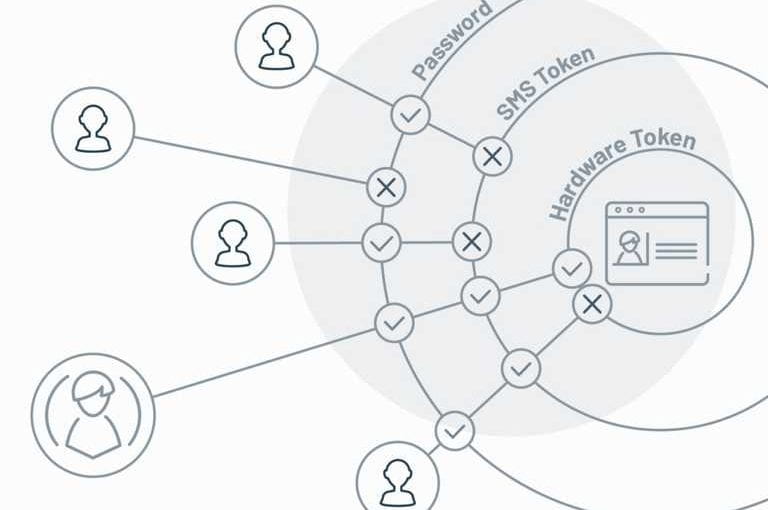
The concept of Multi-Factor Authentication (MFA) revolves around strengthening the security of authentication processes by incorporating multiple layers of verification. At its core, MFA aims to address the vulnerabilities associated with relying solely on traditional username and password combinations. To achieve this, MFA mandates the use of at least two out of three authentication factors: something the user knows (like a password), something they have (such as a smart card or mobile device), and something they are (biometric data). This approach significantly reduces the chances of unauthorized access, thereby bolstering defenses against a wide range of threats, including password breaches and social engineering attacks.
What is an SSO (Single Sign-On)?
“What is SSO?” is a commonly searched query by those seeking a more efficient approach to managing their online access. Single Sign-On (SSO) provides a clear solution by streamlining the authentication process. Through SSO, users authenticate themselves just once through an Identity Provider (IdP), which acts as a centralized authentication system. After verifying the user’s identity, the IdP grants access to multiple applications or systems within the SSO ecosystem. This eliminates the need for users to remember and input credentials separately for each service, simplifying the user experience, improving productivity, and reducing the complexity of managing multiple login credentials.

MFA vs. SSO: What Business Advantages Do They Offer?
Multi-factor authentication (MFA) is about layering security in a way that goes beyond traditional username and password combinations. It adds an extra level of verification by requiring users to provide at least two forms of authentication, making it much more difficult for unauthorized individuals to gain access.
Single Sign-On (SSO) is a transformative authentication approach that merits our attention. It empowers websites and mobile apps to validate user identities through trusted sources. This means that with SSO, users can access different applications using a single set of login credentials, eliminating the need to remember numerous IDs and passwords. SSO plays an indispensable role in the broader context of Identity and Access Management (IAM), which is vital for controlling and managing user access permissions effectively.
Reasons to Choose MFA for Your Business
Multi-factor authentication (MFA) has evolved from being an option to a necessity in the eyes of consumers. It’s no longer a competitive advantage but a baseline requirement for organizations aiming to protect sensitive data and maintain customer trust. Companies that ignore this shift in consumer expectations do so at their own peril.
Here’s what MFA gives you and your consumers:
- Better security
- Boosted conversion
- Improved customer trust
- Reduced operating costs
- Achieve compliance
- Increase flexibility and productivity
Reasons to Choose SSO for Your Business
- Seamless user experience
- More robust password protection
- Reduces customer time
- Improves conversions and revenue
- Mitigates risk
- Unifies customer profiles
- Reduces IT costs
Conclusion
To sum it up, the contemporary business environment necessitates a proactive approach to cybersecurity. The incorporation of Multi-Factor Authentication (MFA) and Single Sign-On (SSO) has become a fundamental requirement to address both security concerns and user experience expectations. For organizations aiming to streamline these technologies effectively, a cloud-based Consumer Identity and Access Management (CIAM) platform offers a holistic solution that can efficiently manage MFA and SSO, ensuring robust security and seamless accessibility.